Top 10 Deadliest Computer Viruses in History: Unveiling the Digital Monsters
The effects of malware can range from maybe a little irk in your head to city-wide power outages and more. (Yes! Hollywood stuff can be real)

Learn about the most destructive malware in history and how to protect your system.
The effects of malware can range from maybe a little irk in your head to city-wide power outages and more. (Yes! Hollywood stuff can be real)
Not another virus! Not again!
We're just surviving somehow amidst a deadly pandemic caused by a virus.
And here we are, writing one more article about deadly viruses.
But hold on! We’re going to talk about computer viruses here.
The reason why all of us install anti-virus software as soon as we buy a computer.
If anything unusual happens to our systems like performance slowdown or unnecessary frequent pop-up windows, the first thing we say- "Oh! Is it a virus?"
It's funny how we're not even safe from viruses online.
Let's first understand what exactly is a computer virus and how it works, and then we'll talk about the 10 deadliest computer viruses ever in human history.
What is a Computer Virus?
A computer virus is an ill-intentioned malicious code/program written to affect the way a computer works. Much like a biological virus, it is capable of reproducing and spreading from one system to another.
It works by attaching itself to a legit program or document. Interestingly, the virus will stay passive in the host until you somehow run the infected program, and then it will show its true colors.
And by true colors, it can cause severe damage to the system software, corrupt files, steal passwords, erase data permanently, and even take over the system completely.
But viruses are not the only type of malware that can damage your computer. Worms and Trojan horses are other malicious programs that can create large-scale problems. Generally, people use all these terms interchangeably but there are minute differences between them you should be aware of.
Viruses cannot infect your system unless you run the program, it cannot spread without human action.
Worms, despite being another sub-class of a virus, can travel from one computer to another without any human action. It is deadlier than a virus as it can create thousands of copies of itself and cause global-scale problems.
That's why most of the viruses on this list are actually worms.
Trojan horse isn't a virus, but a destructive program that looks like a legit application. They don't have the ability to replicate themselves but, don't be fooled as they can be equally damaging. Trojan horses can allow the malicious user to have an access to your computer and steal confidential information like passwords, and account credentials.
The effects of malware can range from maybe a little irk in your head to city-wide power outages and more. (Yes! Hollywood stuff can be real)
With that said, let's look at the top 10 deadliest computer malware to date that wreaked absolute havoc:
10.) Sasser
Written by a 17-year-old German computer science student Sven Jaschan, this virus was so deadly that a bounty of $250,000 was posted on the creator's head. (Yes! Cybercriminals also have bounties)
Sasser was first discovered in 2004 as a Windows worm that would slow down and crash the computer, only to be reset after cutting off the power connection.
Sven Jaschan was eventually arrested at the age of 18, but due to being a minor when he wrote the malware, he received a suspended sentence.
Sasser's impact was significant, affecting millions of PCs and causing disruptions in various businesses and organisations. It left a lasting mark on the cybersecurity landscape.
How did Sasser work?
It leveraged a buffer overflow vulnerability in the Local Security Authority Subsystem Service (LSASS), which controls the security policy of local accounts, thus causing crashes to the computer.
The worm had devastating effects infecting over a million systems. It took out critical infrastructure such as airlines, news agencies, hospitals, public transport, etc.
After causing an estimated $18 billion in overall damages, Jaschan was finally arrested for his friends' tipping. Being 17 years old at the time of creating the worm, he was tried as a minor and faced a 21-month suspended sentence.
9.) Flashback
We all know Macs as the epitome of privacy and security. The Trojan named Flashback proved otherwise, showing that even Macs are not immune.
First discovered in 2011 by the antivirus company Intego, this trojan horse tricked users into installing it by posing as an installer for Adobe Flash. (Beware of fake installers)
Flashback is a striking illustration of the capacity of cyber threats to infiltrate ostensibly fortified systems.
Notably alarming for Mac users, this Trojan capitalised on vulnerabilities within Apple's operating system, afflicting numerous Mac computers across the globe. This incident underscores the critical importance of perpetual vigilance and maintaining current security protocols for all computer users.
How did Flashback work?
Flashback propagated itself by using hacked websites with JavaScript code that downloads the payload.
After infecting one's Mac, it inserted itself into Safari and harvested information from one's web browsing activities, including usernames and passwords.
You didn't even have to manually install anything or enter any admin password anywhere, the trojan slid itself into the system if you merely visited an infected webpage or if you had a vulnerable Java-enabled software.
The scale? More than 600,000 Macs were infected, including 274 in the headquarters of Apple itself.
Apple finally had to release an update for that Java version to remove Flashback from people's Macs and stop the chaos.
8.) Stuxnet
This computer virus was created for cyberwarfare. What has the world come to, right?
It was believed to be a joint operation by the Israeli Defence Force, the American Government, and the CIA to alter the nuclear advancements in Iran. This malware attack targeted the programmable logic controllers (PLCs) that are used to automate machine processes.
The Stuxnet virus was a remarkable example of state-sponsored cyberwarfare, showcasing the increasing complexity of modern digital threats. Its precise targeting of Iran's nuclear infrastructure demonstrated the potential for strategic disruption through cyber means. The covert nature of such operations underscores the evolving landscape of global security challenges.
According to estimates, one-fifth of Iran's nuclear centrifuges were ruined by this deadly worm.
How did Stuxnet work?
It was a multi-part worm that spread across Microsoft Windows PCs and traveled on USB drives.
It searched for PLCs (specifically for the presence of Siemens Step 7 software; a software used by PLCs to automate and monitor electro-mechanical hardware).
Once it took over a PLC computer, it would update its code and send damage instructions to the equipment controlled by the PLC computer.
On the other side, it sent false feedback to the central controller so people wouldn't have a clue of what was going on until the hardware started to self-destruct.
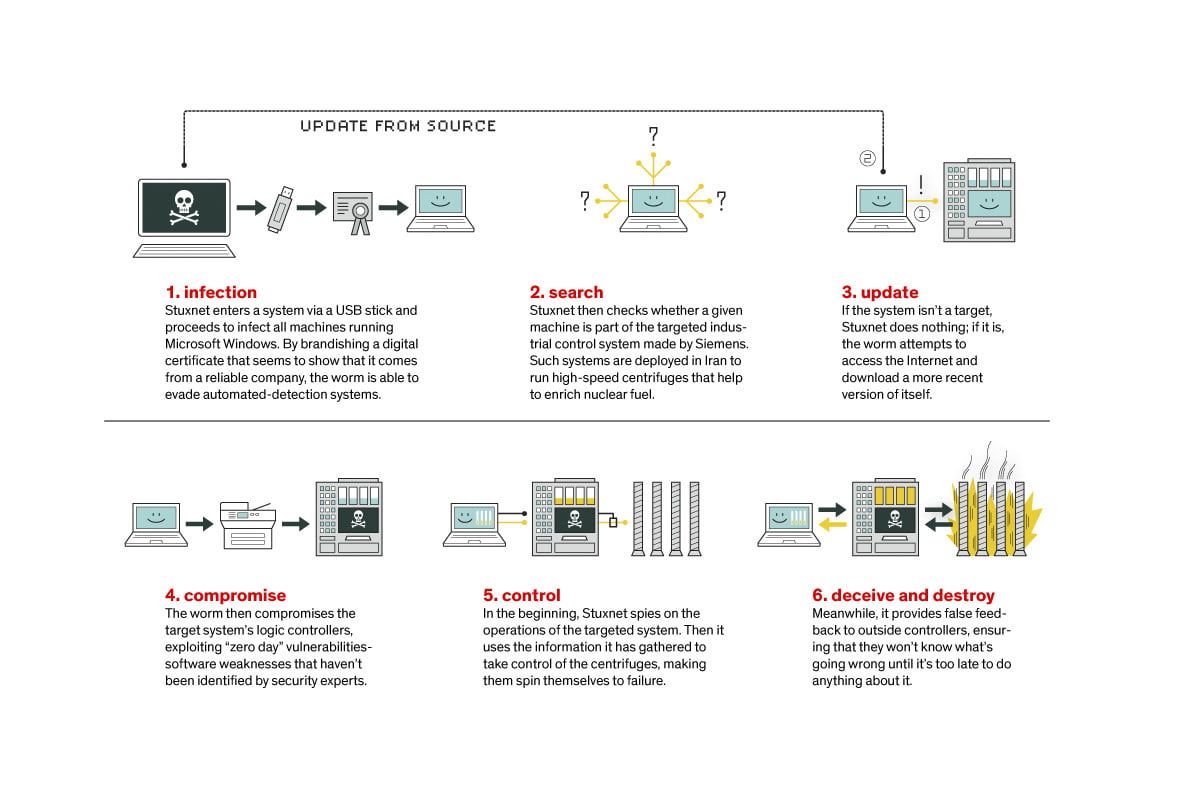
Stuxnet, discovered in 2010 is potentially the first ever virus to be capable of affecting hardware.
Siemens somehow figured out a way to remove the malware from their software.
But many other groups have modified the virus over time and targeted facilities like power plants, and water treatment plants, among other huge machines.
7.) CryptoLocker
CryptoLocker was a Trojan ransomware attack that infected north of 500,000 computers running on windows.
It encrypted the files and displayed a red ransom note asking for money in exchange for the encryption/unlock key. (And we thought only kidnappers asked for ransom)
The ransom asked generally amounted to $400 in prepaid cash or bitcoin. Adding a layer of anonymity for the cybercriminals behind this malware. The widespread impact and financial losses caused by CryptoLocker underscored the evolving tactics of cybercriminals in the digital age.
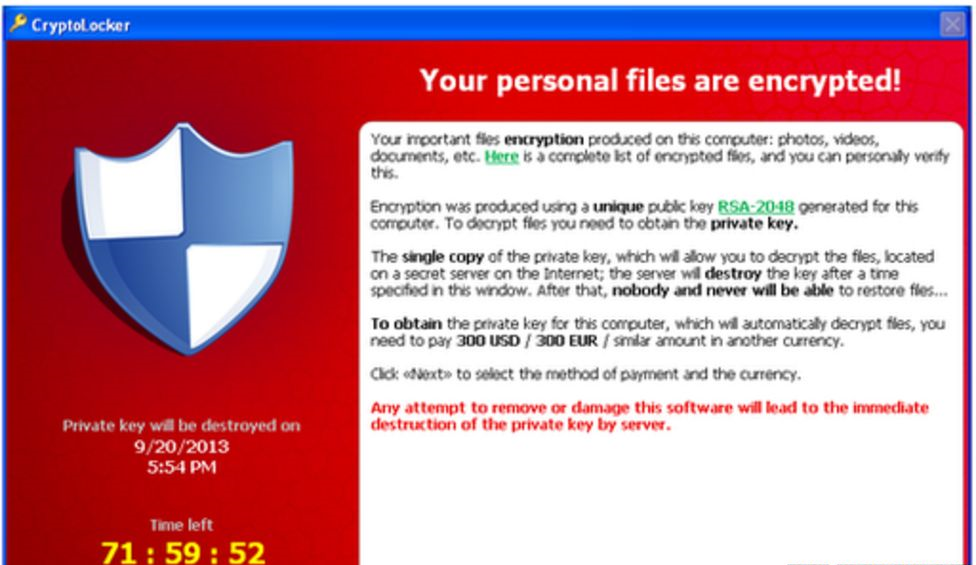
How did CryptoLocker work?
It spread through emails and several other mediums. Upon infecting a computer, CryptoLocker would lock important files on the drive or any other connected storage device using the RSA public key cryptography.
Law enforcement agencies finally came to the rescue, seizing control of the botnet operating CryptoLocker.
Evgeniy Bogachev, the creator of CryptoLocker was arrested and charged, and the encryption keys were given to the affected computers. But not before affecting over 500,000 systems, causing approx $665 million in damage.
6.) Conficker
As interesting as it sounds, this devastating worm is known to have infected more than 9 million computers across the globe, including governments, businesses, and individuals.
Making its first appearance in 2008, Conficker used the flaws in Windows OS to create a botnet and infect systems. This notorious computer worm wreaked havoc on a global scale, infecting millions of computers and causing substantial damage. However, exact financial figures remain elusive due to its complexity and extensive reach.
How does Conficker work?
Also known as Downup/Downadup, it works by exploiting a network service issue present in Windows. Upon infection, the worm would change account lockout policies, block Windows updates, and log out user accounts, among many other paths. Eventually, the system would become a botnet slave and scam money off the users.
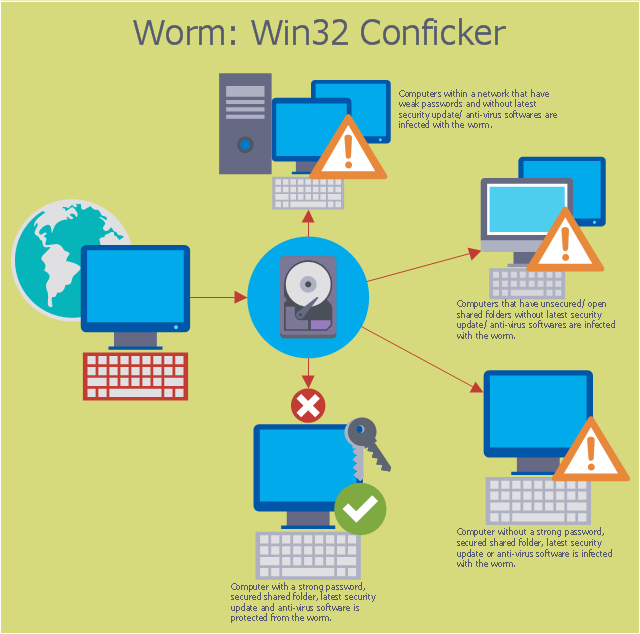
The good news is that Microsoft came up with a fix to tackle Conficker as many antivirus vendors provided updates to their products.
The total damage done by Conficker was estimated at a staggering $9 billion.
Honestly, this amount wouldn't seem staggering as we move on to the top 5 in the list. Still, tuned in?
5.) Code Red
This virus has maybe the most interesting background story to its name. Two eEye Digital Security employees were drinking Code Red Mountain Dew when they came up with the discovery in 2001.
Estimated to have penetrated over 975,000 hosts/servers, Code Red also caused a DDoS attack on the U.S White House's website. Additionally, Code Red's rapid spread and the defacement of websites with the message "Hacked by Chinese!" raised concerns about cybersecurity vulnerabilities at the time. It highlighted the importance of robust security measures in safeguarding critical online infrastructure. (Now, that's pretty big!)
How did Code Red work?
This worm targeted systems that had the Microsoft IIS web server installed and leveraged a buffer overflow issue in the system.
Code Red had tremendous multiplicity as it made hundreds and thousands of copies of itself, eating up a lot of system resources.
Interestingly it displayed the message - Hacked By Chinese on the affected web pages.
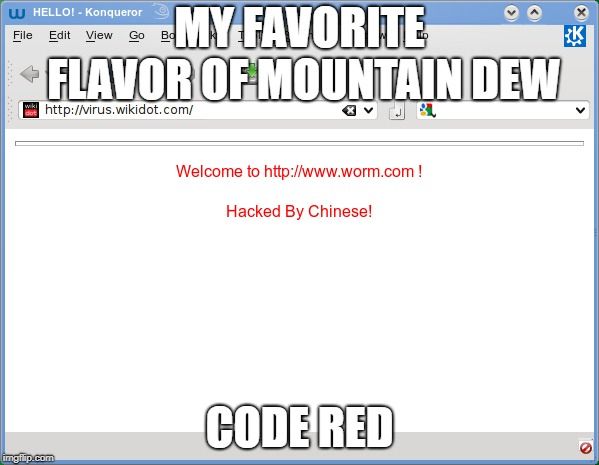
The White House had to change its IP address to tackle this virus.
According to estimates, Code Red caused $2 billion in total damage and shook up the entire world as a bonus.
4.) Zeus
Seriously who names these viruses such interesting names? (Maybe we should write another article on that?)
Zeus, also known as Zbot is a crimeware kit designed to steal users' online banking details and other important information in order to transfer money to secret bank accounts. It hit the web in 2007 and immediately caught speed, being the reason for 44% of all banking malware attacks over the next 3 years.
It is a Trojan that can secretly install itself on your device. Zeus is a prime example of how cybercriminals use sophisticated techniques to compromise personal and financial security, making it essential for users to stay vigilant and employ robust cybersecurity measures.
How does Zeus work?
Generally, it's delivered through phishing emails. Once it has infiltrated the system, it can affect systems in two ways-
- It can add your system to a network of infected devices referred to as Zeus botnet, and leverage this group of computers to launch DDoS attacks on other targets.
- Or it can steal sensitive information directly from your device and direct it to cybercriminals who would be more than ready to empty your bank accounts, and whatever they get their hands on.
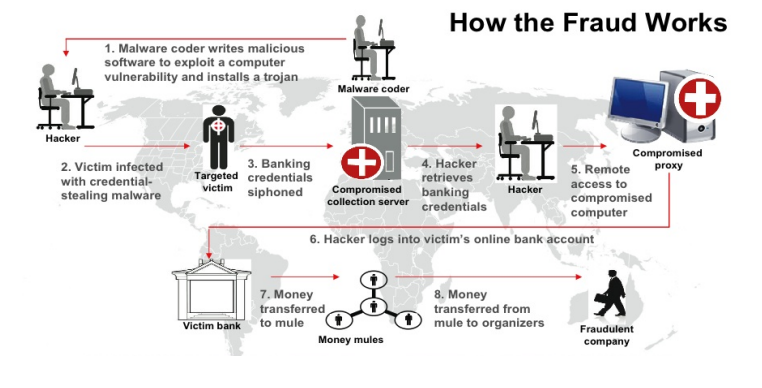
The source code of Zeus Trojan was released to the public in 2011 (intentionally or leaked, we don't know) that allowed the creation of multiple variants, some of which are still active today, such as the likes of SpyEye, Gameover Zeus, and Ice IX, etc.
Zeus and its new variants have targeted large-scale organizations such as Amazon, NASA, and Bank of America. In just 3 years, it had already breached 88% of Fortune 500 companies, and about 75,000 computers spanning over 200 countries.
We wouldn't have a definite amount but if we combine all financial, productivity, and goodwill losses, the overall damage would be somewhere around $3.8 billion.
3.) WannaCry
Yet another intriguing name! WannaCry began with a cyber attack on May 12, 2017, and affected lakhs of computers in over 150 countries.
It was an attack truly of epidemic sorts.
WannaCry is a worm, meaning it requires no participation from the victim (not even a click) and can spread automatically, unlike other ransomware variants that spread through phishing emails or other methods.
In the aftermath of the extensive repercussions caused by WannaCry, it took advantage of weaknesses in obsolete Windows operating systems, with a particular focus on the National Health Service (NHS) in the United Kingdom, ultimately causing damages close to $120 million. This incident highlighted the importance of maintaining up-to-date software in our progressively interconnected digital landscape.
How did WannaCry work?
It spreads using the EternalBlue exploit leaked by the National Security Agency (NSA). The exploit enables an attacker to transfer crafted packets to any device that accepts data from the public internet on port 445.
Once a system is infected, the worm multiplies itself and affects other unpatched devices, not needing any human interaction.
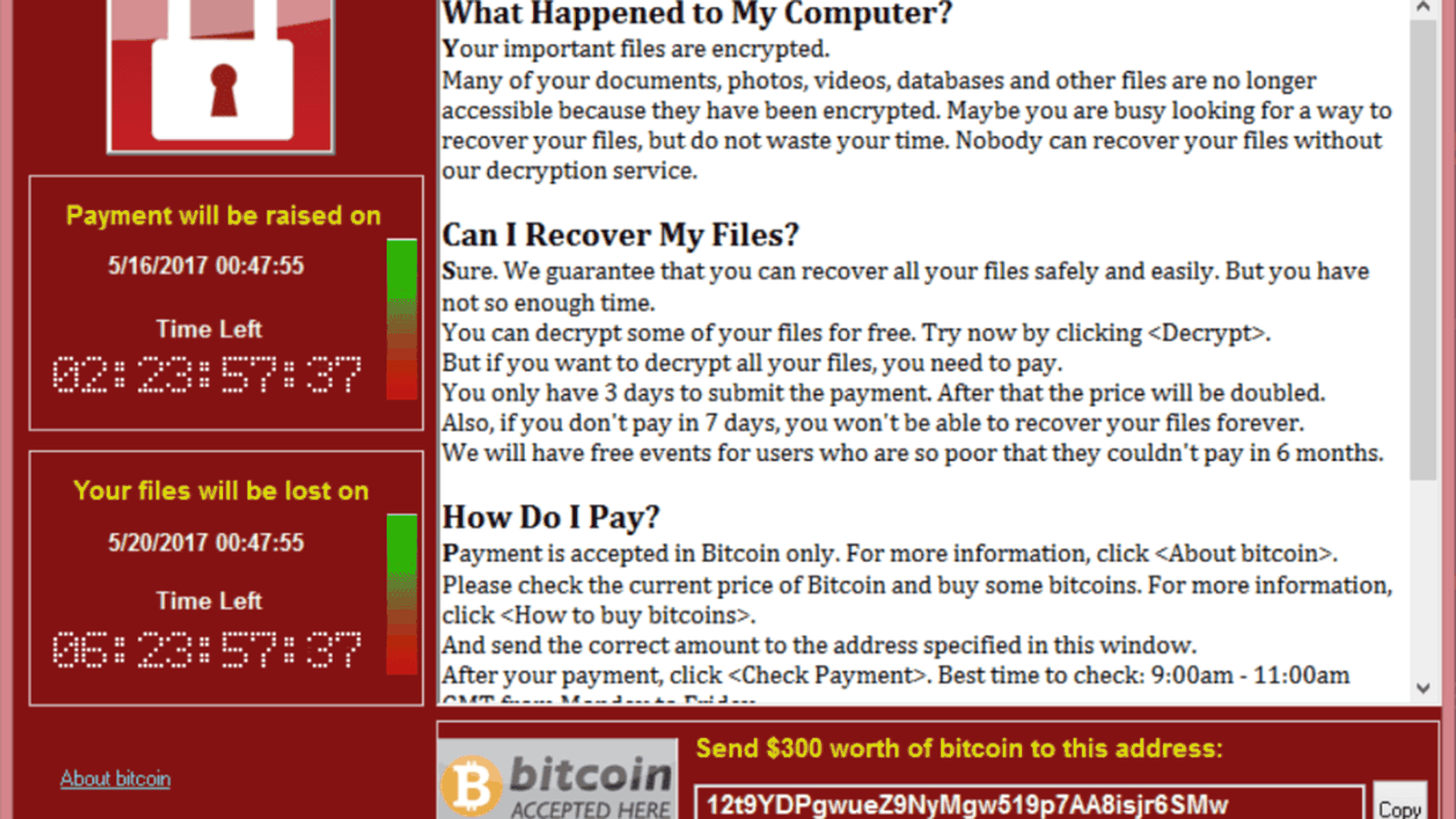
After encrypting the files of Windows devices, this crypto-worm demanded a ransom of $300 to $600 in Bitcoin in exchange for the decryption key. What's even worse is that most of the people didn't get the key even after making payments.
The worm majorly affected out-of-date Windows systems. As a result, Microsoft initiated an unexpected step of releasing patches for end-of-life versions of Windows.
In the initial attack, WannaCry created absolute chaos for businesses and individuals across the globe.
The overall damage in financial terms, as estimated by Broadcom, reached $4 billion.
It could have been even more catastrophic if not for a certain 22-year-old security researcher Marcus Hutchins who developed a kill switch that stopped the worm from spreading.
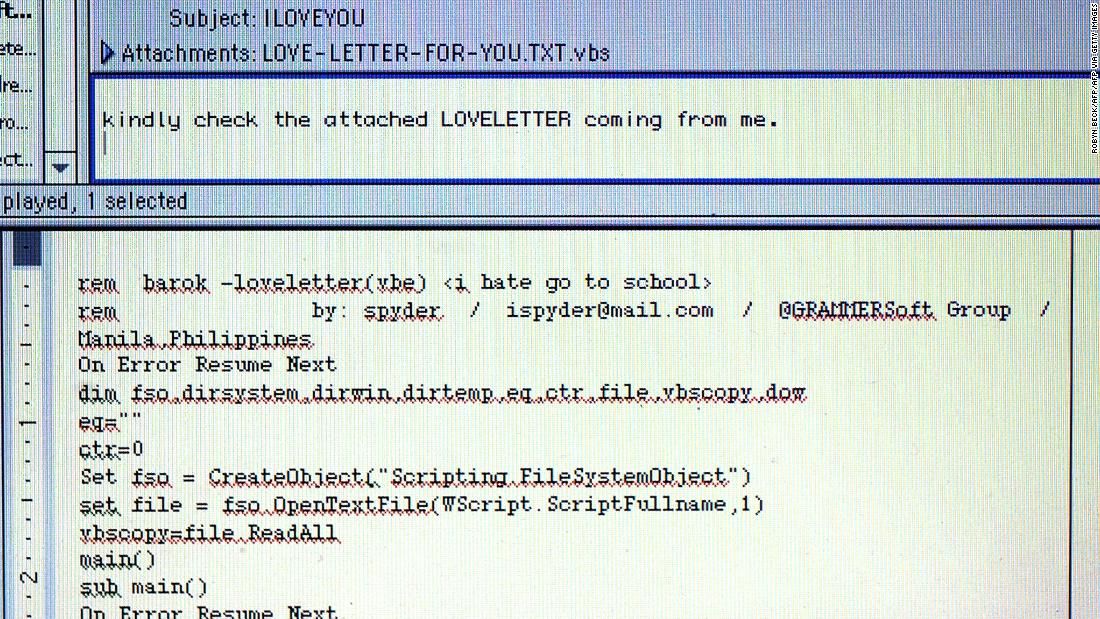
2.) I LOVE YOU
Next time you receive a love letter, beware as it could contain a virus. Jokes apart, the ILOVEYOU virus aka the love bug is believed to be one of the most malicious and virulent computer viruses ever created on the face of the planet.
It knocked on the user’s door in the form of an email with the subject line ‘I love you.’ The message contained an attachment ‘LOVE-LETTER-FOR-YOU.txt.vbs.
This notorious virus quickly spread like wildfire, infecting over 45 million computers worldwide within a mere ten days. Its global rampage included high-profile victims such as the Pentagon, CIA, and the UK Parliament. The ILOVEYOU virus left an indelible mark, causing an estimated financial damage of over $10 billion during its reign of digital chaos.
How does ILOVEYOU virus work?
Windows at the time couldn’t display the actual extension of the file and users were trapped considering it to be a plain text file. Once opened, the Visual Basic Script would then get activated and take over the local computer overwriting files by itself, and making the computer unbootable. It would also send itself to the user’s entire mailing list, thus spreading way faster than any other email worm.
The ILOVEYOU virus was created by two Filipino programmers - Reonel Ramones and Onel De Guzman. Interestingly enough, the sole purpose of the virus was to steal others’ passwords in order to get free internet access. Little did they know that the virus they had created would spread worldwide and end up infecting almost 10% of the world’s computers.
Yes! Such was the scale of the disaster that the government and many large organizations shifted to an offline mailing system to prevent any infection.
Breaking out on May 4, 2000, it infected north of 45 million PCs starting from Hong Kong and then moving to Europe and the US. The overall damage was estimated to be over $10 billion dollars.
Note- The two programmers were never charged due to the absence of malware laws. The widespread led to the enactment of the E-Commerce law to address any such issues in the future.
1.) MyDoom
Here comes the biggest, and the most malicious of all computer viruses- MyDoom.
This juggernaut started rolling in January 2004, with people all around the world getting mysterious emails that said, "I'm just doing my job, nothing personal, sorry."
MyDoom, also known as Novarg, was a devastating computer virus that wreaked havoc in 2004. It is infamous for its widespread impact and the massive financial damage it caused.
The virus spread rapidly through mass emails, making it one of history's most notorious cyber threats. Its ability to generate billions of dollars in estimated costs underscores the immense destructive power of MyDoom.
How does MyDoom work?
It worked in a similar way as the love bug; scraping email addresses from infected Windows computers and sending a new version of itself to those contacts. Every time the attachment was opened, the virus would spread to more and more victims.
And not just that, the doom virus would then rope all these infected systems into a botnet and carry out large-scale DDoS attacks on some of the largest companies in the world.
At one point in time, the worm generated up to 25% of all emails being sent worldwide. Now, that's some scale!
Such was the impact of the virus that even Google's shop was shut on 26 July 2004 as users couldn't conduct web searches for one whole day. It also affected other search engines at the time such as Yahoo and Alta Vista.
According to reporters, the virus was fast, effective, and expensive. The estimated damage caused by MyDoom reached up to $39 billion.
The second version of the worm had one more shocking ability - After infecting a computer, it would block its access to 65 antivirus websites, and keep users from cleaning their computers.
MyDoom is still active to this day, and according to an analysis by Unit 42- It constituted 1% of all phishing emails circulated around the globe in 2019.
It could be anywhere and attack you with basic subject lines like 'hello', 'failed delivery notification', or 'click me baby, one more time, etc.
Final Thoughts
So, there it was! A list of the 10 most dreaded malicious software in all of human history. There are many more who couldn’t make the list but are equally dangerous. So, here are a few notable mentions-
Sobig- Second only in scope to MyDoom, this worm broke out in 2003 and caused an overall loss of $30 billion worldwide. Posing as legit software, Sobig disrupted the ticketing at Air Canada and affected several other businesses.
Slammer - The SQL Slammer worm used the infected machines to cause DDoS attacks on several internet hosts, hitting banks in the US and Canada, and taking ATMs offline in many places.
Storm Worm - "230 dead as storm batters Europe." This is how the storm worm got its prospects to open the attachment, subsequently attacking millions of computers. The Storm Worm used deceptive email subject lines like "230 dead as storm batters Europe" to lure unsuspecting users into opening its malicious attachments, leading to widespread computer infections and significant damage.
Yaha - Thought to be the result of cyber warfare between India and Pakistan, this is yet another worm that arrived in the form of .exe or .scr in email attachments. It spread rapidly by exploiting vulnerabilities in Windows systems and remains one of the most costly cyberattacks in history, significantly impacting businesses and organisations across the globe.
Melissa - Created in 1999, it started in the form of an infected word document and lured people in by claiming to have a list of passwords for pornographic sites. Interestingly, it was named after an exotic dancer from Florida.
In fact, a staggering 6000 computer viruses are created and released every month. Tough times to live, isn’t it?
We know that we’ve sparked enough fear in you, but that was never our intention. The purpose was to get you acquainted with different types of malicious programs so you can protect your system and important data.
And that’s why we prepared a list of tips and actionable steps for you to prevent such attacks:
- Keep your software updated with the latest versions
- Install quality antivirus software
- Don’t download software from unreliable sources
- Don’t click on links within emails from unknown/anonymous sources
- Back up your data regularly
- Use pop-up blockers
- Create strong passwords (a mix of letters, numbers, and symbols are the best bet)
- Scan your computer if you sense symptoms (strange errors, odd system shutdowns, slow performance, etc. can all be symptoms of a virus looming around)
Today, preventing malware attacks is not as difficult as it used to be. Make sure you follow these steps and you will be glad that you did.
FAQs
What are computer viruses, worms, and Trojan horses?
- Computer viruses are malicious codes that attach to legitimate programs and require user action to spread.
- Worms are self-propagating viruses that spread without user intervention.
- Trojan horses masquerade as legitimate applications but are harmful.
How can I protect my computer from viruses?
To protect your computer from viruses, follow these steps:
- Keep your software updated.
- Install reputable antivirus software.
- Avoid downloading software from unreliable sources.
- Be cautious of email attachments and links from unknown sources.
- Regularly back up your data.
- Use pop-up blockers.
- Create strong, unique passwords.
- Scan your computer for viruses if you notice unusual behaviour.

